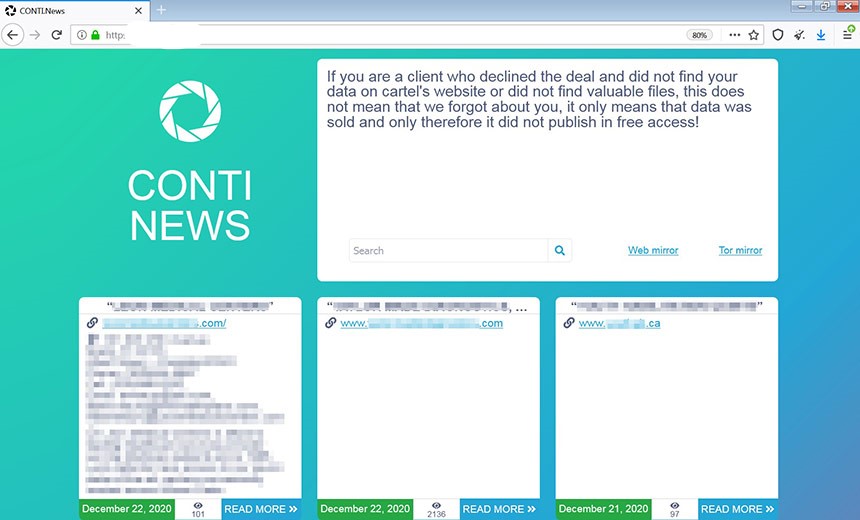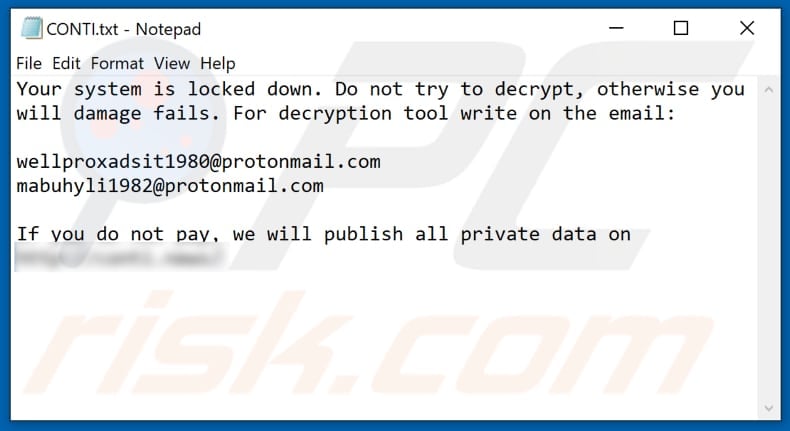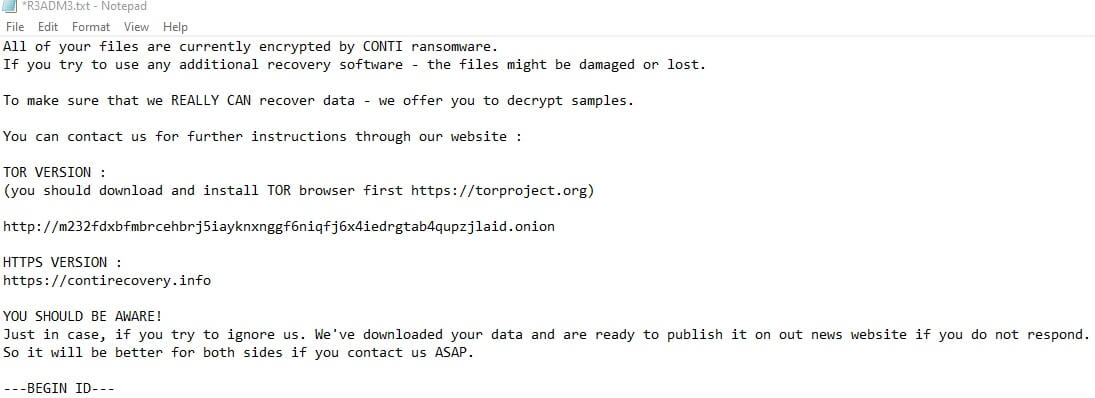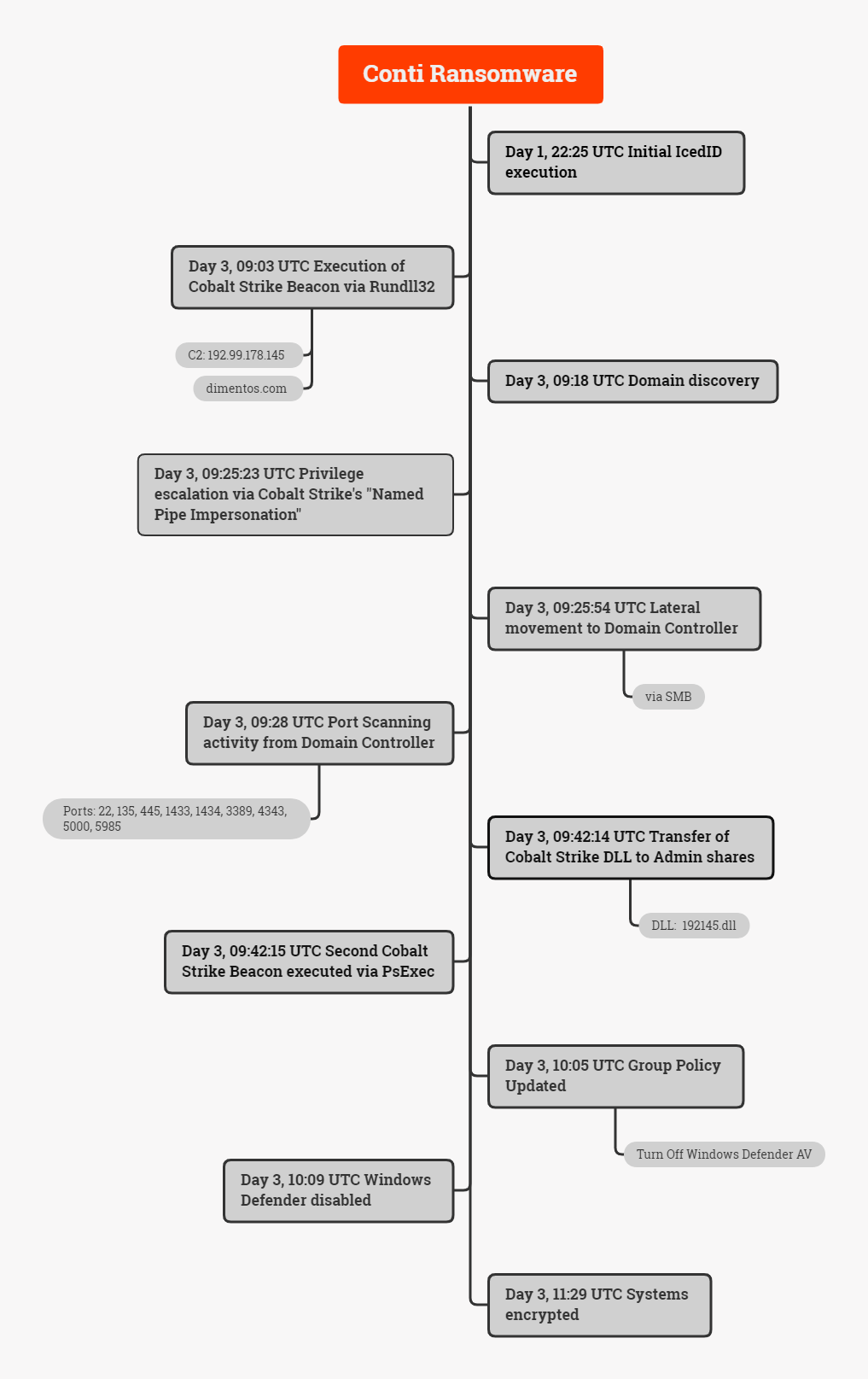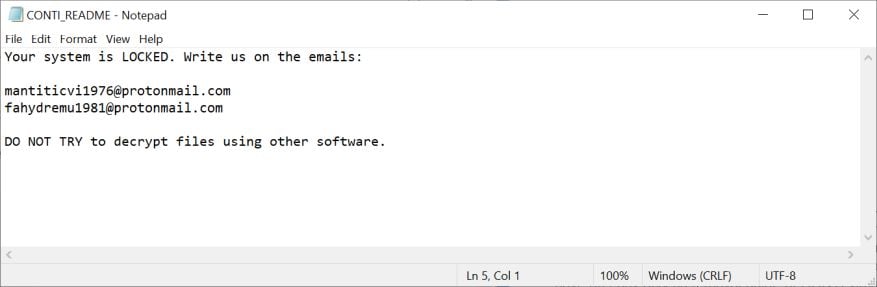
CONTI Ransomware - Entschlüsselung, Entfernung und Wiederherstellung verlorener Dateien (aktualisiert)
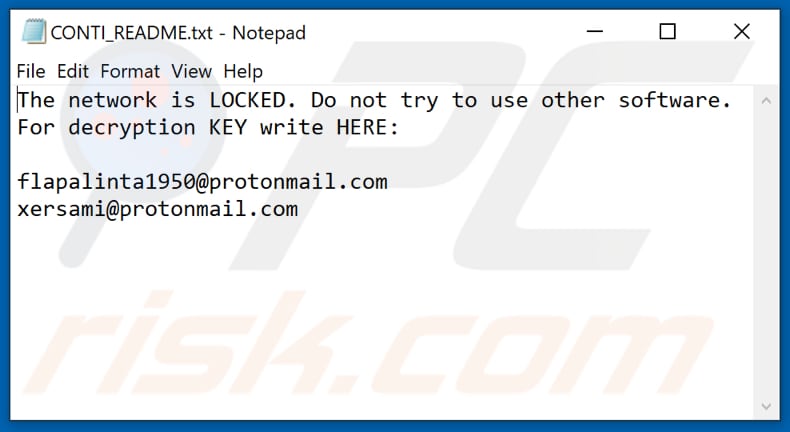
CONTI Ransomware - Entschlüsselung, Entfernung und Wiederherstellung verlorener Dateien (aktualisiert)
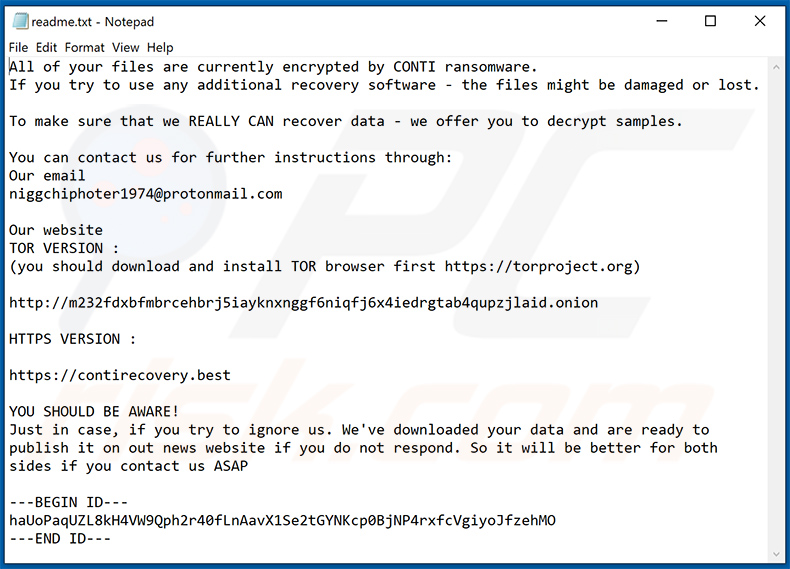
CONTI Ransomware - Entschlüsselung, Entfernung und Wiederherstellung verlorener Dateien (aktualisiert)
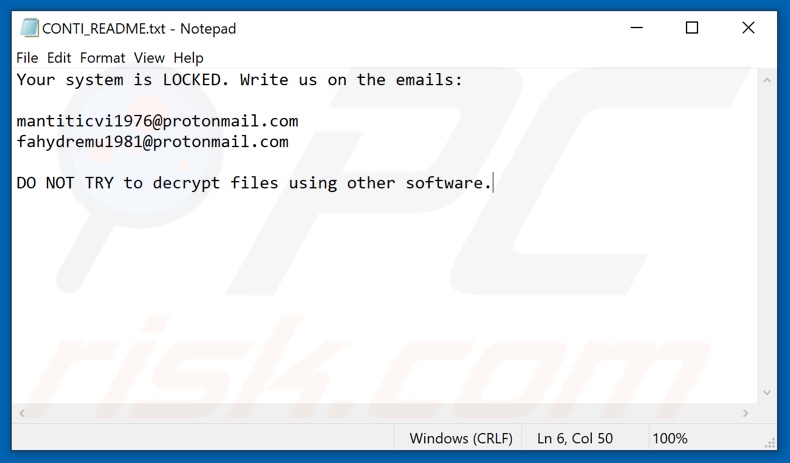
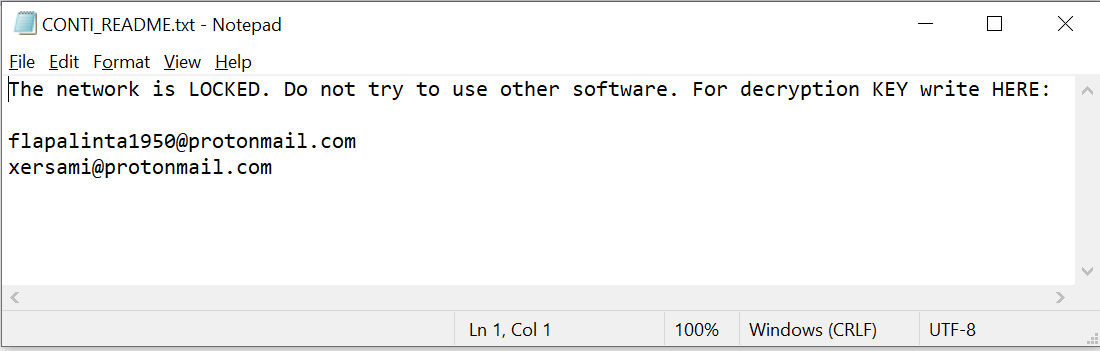

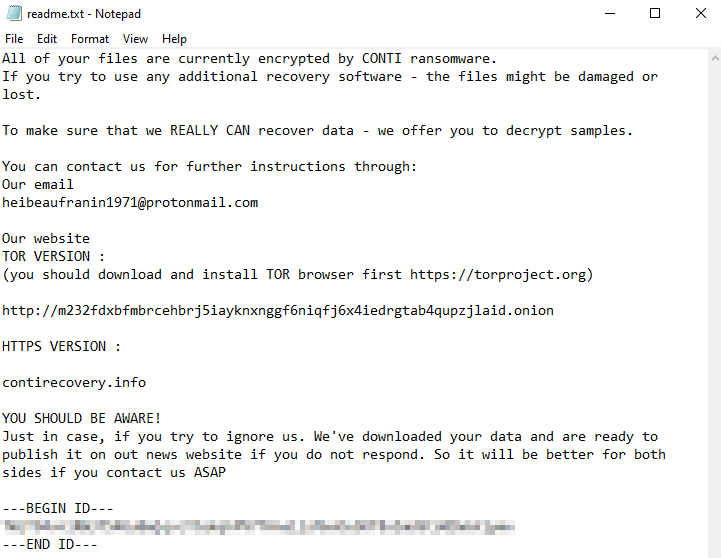

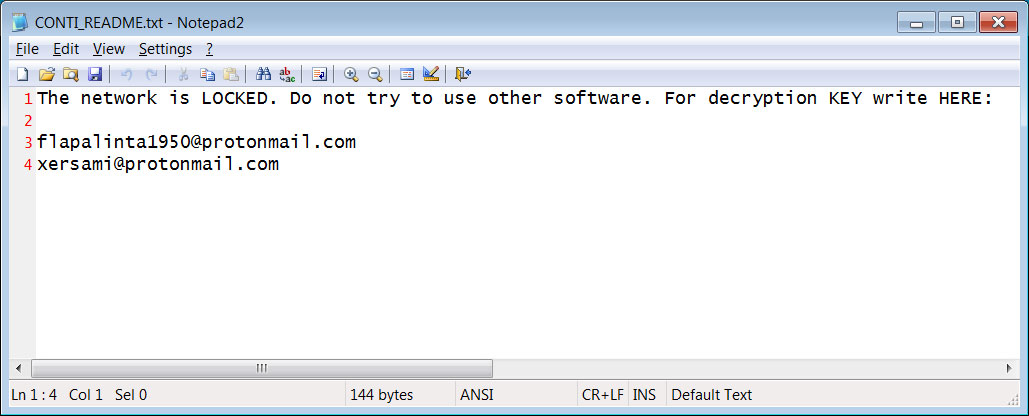
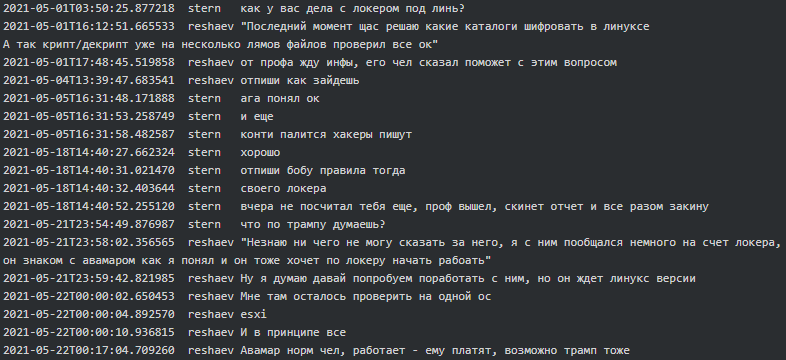
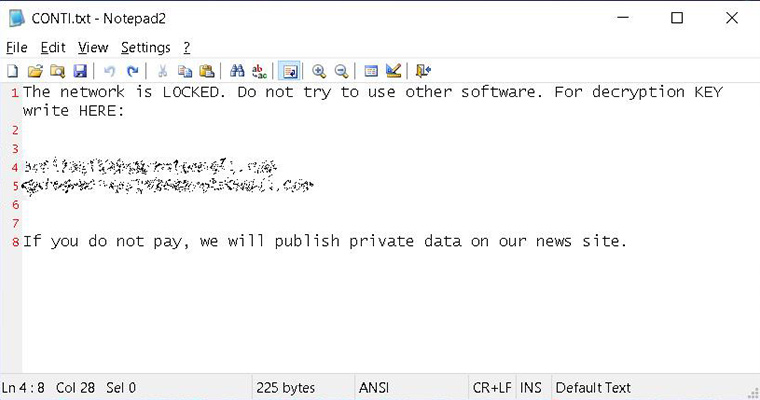




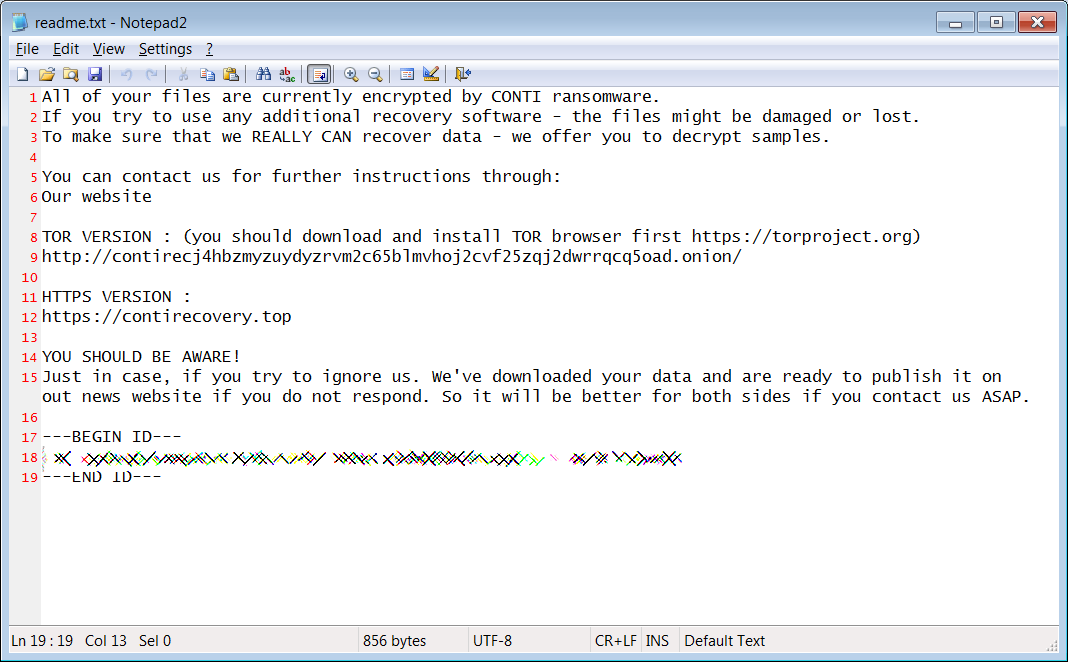

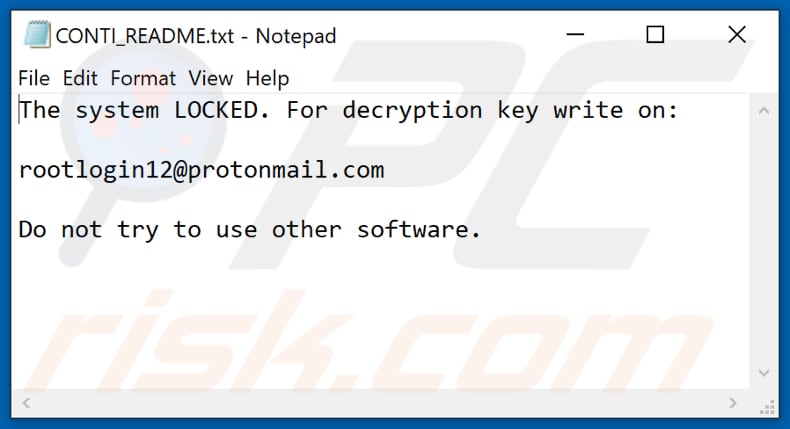
![SYTCO-Virendatei - Ransomware-Konten [So entfernen Sie] SYTCO-Virendatei - Ransomware-Konten [So entfernen Sie]](https://sensorstechforum.com/wp-content/uploads/2020/12/stf-SYTCO-file-virus-conti-ransomware-note.jpg)