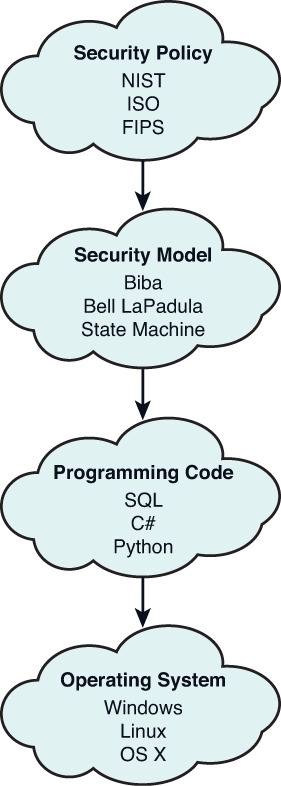
Figure 2.5 from Access control policies and companies data transmission management. (Gestion du contrôle de la diffusion des données d'entreprises et politiques de contrôles d'accès) | Semantic Scholar
Evaluation of the Appropriateness of Trust Models to specify Defensive Computer Security Architectures for Physical Protection S
Bell Lapadula Security Ppt Powerpoint Presentation Professional File Formats Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
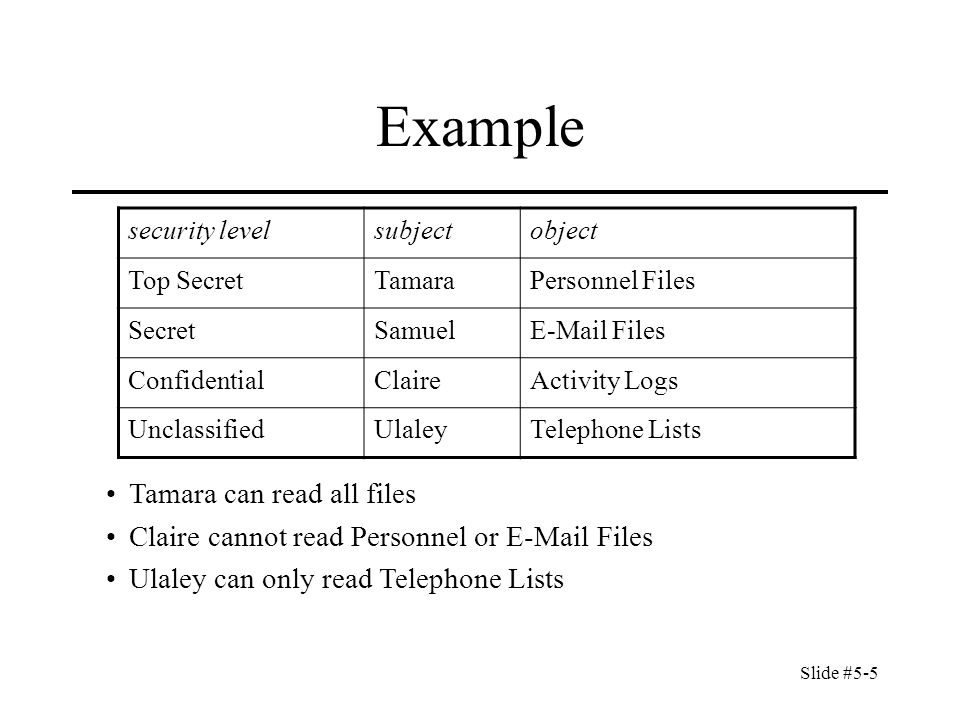
Slide #5-1 Chapter 5: Confidentiality Policies Overview –What is a confidentiality model Bell-LaPadula Model –General idea –Informal description of rules. - ppt download

Bell Lapadula Confidentiality Model Ppt Powerpoint Presentation Gallery Graphics Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
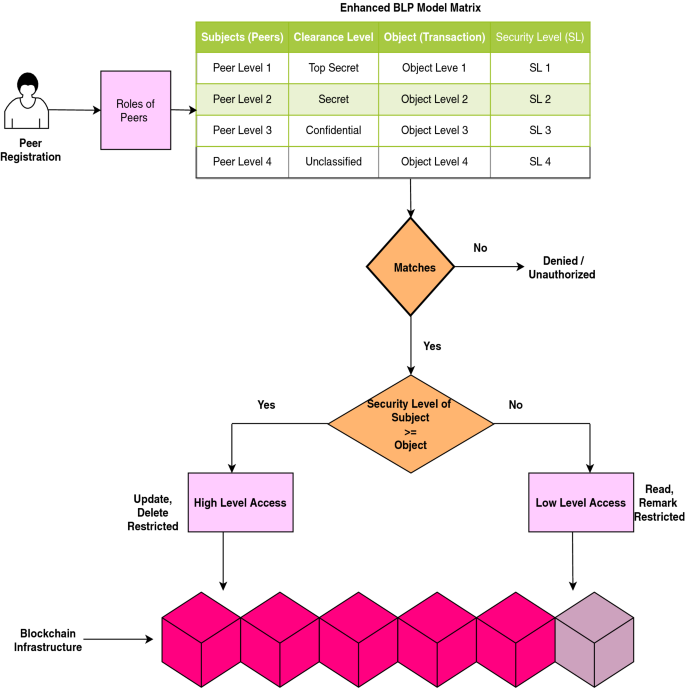











![Information Security Series: [Part2] Principles of Privileges Information Security Series: [Part2] Principles of Privileges](https://cdn.hashnode.com/res/hashnode/image/upload/v1647290827356/3qC3AeROC.png?auto=compress,format&format=webp)